System Design .
Antenna Design.
Image Processing Using
Open-CV.
read more
PROJECTS IDEAS
HELP SHARE IDEAS.COM
Mail us at : info@helpshareideas.com
Face Based Smart RFID Security And Attendance System With Audio Acknowledgement using Arduino
Face based detection of the people is very helpful to ascertain their identity. We are proposing a system in which the employee data is created in the company or any other institutional database. The photo will be uploaded into the database as well. First we need to detect the faces from the live video streaming from the camera. Using suitable face detection algorithms, the face matching is done with the employee when he enters into the campus from the live video captured by the cameras. This step acts as first layer of security for the sensitive places. If match of the face does not happen then alarm gets triggered & security guards will take action.
If the face of the person entering campus matches with the available database, his Bio-metric finger print authentications is taken. If the finger prints match then an automatic attendance update is done with respect to his employee ID card number found in the database with the entry time & date details. Every time he needs to swipe his ID card both for gaining access into the campus as well as while exit.
With this kind of system we can restrict the unauthorized use of ID cards as we are using face detection technology too in the proposed system. Dual or multi people entry with single access card too can be prevented.With the help of the Finger print based bio metric authentication, we can add multi-layer security system to the concerned sensitive establishments. Finger print based attendance is common now a days in all institutional and research establishments.
In this project we will focus on face based authentication with bio metric system.
Proposed Solution
Web camera captures the live video& from the live video, the frames from the live video are processed for the face detection first. Once face is detected, then the face of the employee captured is matched with the face of the concerned employees face photo already present in the database which has been tagged for the particular employee ID number. Once all the parameters match then the left hand thumb finger print is taken and it is also checked for authentication. If found matched then the Attendance is marked in the file with the log in details
About Arduino Uno Microcontroller
Any electronic product that needs computation or interfacing with other computers first requires a quick prototyping of the concept using simple tools. Arduino is an open source hardware prototyping platform designed around a popular microcontroller family, and it includes a simple software development environment. Besides prototyping, you can also use Arduino for the development of your own do-it-yourself (DIY) projects. Arduino bridges the computational world with the physical world by letting you simply connect the sensors and actuators with a computer. Basically, you can write code to monitor and control various electronic components in your daily life by using Arduino's input/output pins and microcontroller. Examples of these components include motors, thermostats, lights, switches, and many more.
Why Arduino?
- The major goal of the Arduino community is to continuously improve the Arduino platform with the following objectives in mind:
- The Arduino platform should be an affordable platform
- It should be easy to use and easy to code
- It should be an open source and extensible software platform
- It should be an open source and extensible hardware platform
- It should have community-supported DIY projects
The Arduino Uno board
As Uno is going to be the de facto board for the projects, let's get ourselves familiar with the board. The latest revision of the Uno board is based on Atmel's ATmega328 microcontroller. The board extends the I/O pins of the microcontroller to the peripheral, which can then be utilized to interface components using wires. The board has a total of 20 pins to interface, out of which 14 are digital I/O pins and 6 are analog input pins.
From the 14 digital I/O pins, 6 pins also support pulse-width modulation (PWM), which supports the controlled delivery of power to connected components. The board operates on 5V. The maximum current rating of the digital I/O pins is 40 mA, which is sufficient to drive most of the DIY electronic components, excluding motors with high current requirements.
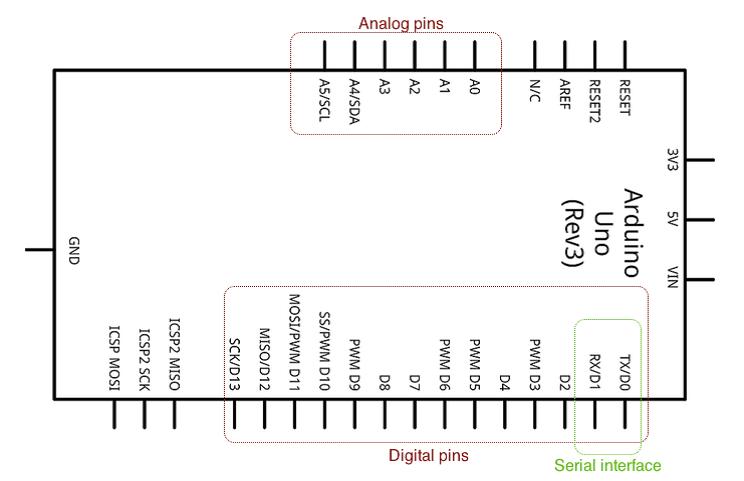
Fig 1: Arduino PIN Diagram
While the previous image provided an overview of the Uno board, the following diagram describes the pins on the Uno board. As you can see, the digital pins are located on one side of the board while the analog pins are on the opposite side. The board also has a couple of power pins that can be used to provide 5V and 3.3V of power to external components. The board contains ground pins on both sides of the board as well. We will be extensively using 5V of power and ground pins for our projects. Digital pins D0 and D1 support serial interfacing through the Tx (transmission) and Rx (receiver) interfaces respectively. The USB port on the board can be used to connect Arduino with a computer.
RFID Reader
In a basic RFID system, tags are attached to all items that are to be tracked. These tags are made from a tiny tag-chip, sometimes called an integrated circuit (IC), that is connected to an antenna that can be built into many different kinds of tags including apparel hang tags, labels, and security tags, as well as a wide variety of industrial asset tags. The tag chip contains memory which stores the product's electronic product code (EPC) and other variable information so that it can be read and tracked by RFID readers anywhere.

Fig 2: RFID Reader module
An RFID reader is a network connected device (fixed or mobile) with an antenna that sends power as well as data and commands to the tags. The RFID reader acts like an access point for RFID tagged items so that the tags' data can be made available to business applications.
FINGER PRINT SENSOR
Fingerprint identification is one of the most well-known and publicized biometrics. Because of their uniqueness and consistency over time, fingerprints have been used for identification for over a century, more recently becoming automated (i.e. a biometric) due to advancements in computing capabilities. Fingerprint identification is popular because of the inherent ease in acquisition, the numerous sources (ten fingers) available for collection, and their established use and collections by law enforcement and immigration.

Fig 3: Finger Print Sensor module
A fingerprint usually appears as a series of dark lines that represent the high, peaking portion of the friction ridge skin, while the valleys between these ridges appears as white spaceand are the low, shallow portion of the friction ridge skin. Fingerprint identification is based primarily on the minutiae, or the location and direction of the ridge endings and bifurcations (splits) along a ridge path. The images below present examples of fingerprint features: (a) two types of minutiae and (b) examples of other detailed characteristics sometimes used during the automatic classification and minutiae extraction processes.
The types of information that can be collected from a fingerprint’s friction ridge impression include the flow of the friction ridges (Level 1 Detail), the presence or absence of features along the individual friction ridge paths and their sequence (Level 2 Detail), and the intricate detail of a single ridge (Level 3 Detail). Detection is usually based on the first and second levels of detail or just the latter. AFIS technology exploits some of these fingerprint features. Friction ridges do not always flow continuously throughout a pattern and often result in specific characteristics such as ending ridges, dividing ridges and dots, or other information. An AFIS is designed to interpret the flow of the overall ridges to assign a fingerprint classification and then extract the minutiae detail – a subset of the total amount of information available yet enough information to effectively search a large repository of fingerprints.
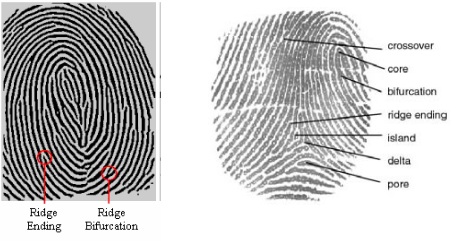
Fig 4: Finger Print Characteristics
Hardware
A variety of sensor types — optical, capacitive, ultrasound, and thermal — are used for collecting the digital image of a fingerprint surface. Optical sensors take an image of the fingerprint, and are the most common sensor today. Thecapacitive sensor determines each pixel value based on the capacitance measured, made possible because an area of air (valley) has significantly less capacitance than an area of finger (friction ridge skin). Other fingerprint sensors capture images by employing high frequency ultrasound or optical devices that use prisms to detect the change in light reflectance related to the fingerprint. Thermal scanners require a swipe of a finger across a surface to measure the difference in temperature over time to create a digital image.
Software
The two main categories of fingerprint matching techniques are minutiae-based matching and pattern matching. Pattern matching simply compares two images to see how similar they are. Pattern matching is usually used in fingerprint systems to detect duplicates. The most widely used detection technique, minutiae-based matching, relies on the minutiae points described above, specifically the location and direction of each point.
Block Diagram of proposed face & Bio metric Based attendance & Security system
The block diagram has been given in below fig. Inbuilt webcam along with speakers of the PC or laptop has been used along with other hardware components such as Arduino UNO, Finger print sensor, RFID reader, Buzzer etc.
Now a days we come across finger print based attendance system. In the proposed system we have integrated the advantages of RFID and Bio-metric with the face detection techniques, thus providing a three layer full proof security system useful for any sensitive establishments.
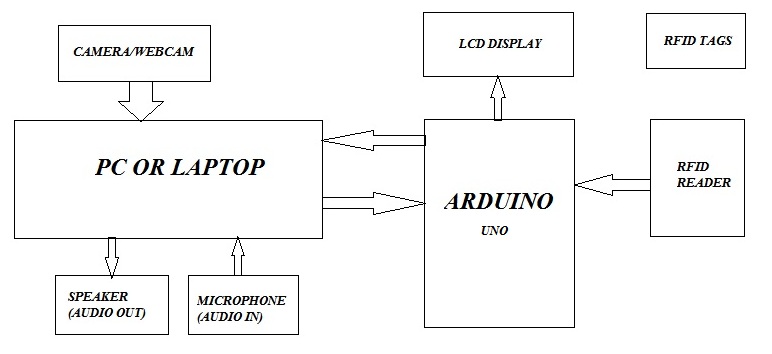
Fig 5: Block Diagram of proposed system
Web camera captures the live video frames & the frames from the live video are processed for the face detection first. Once face is detected, then the employee is asked to swipe his Employee ID card. Those details are captured. Then the captured ID number is matched with the Employee ID s already present in the database. Once all the parameters match then the left hand thumb finger print is taken and it is also checked for authentication. If found matched then the Attendance is marked in the file with the log in details.
RFID reader is a device that provides the connection between the Employee ID tag data and the processing system that needs the information. The reader communicates with tags that are within its field of operation. The RFID reader uses an attached antenna to capture data from tags. It then passes the data to a system for processing. Just like RFID tags, there are many different sizes and types of RFID readers. RFID Readers can be integrated into a Machine device such as an embedded portable system we are discussing here to make use of it for reading the Employee ID card tag numbers.
To make our proposed design low cost we have used the inbuilt web camera, speakers and microphone of the laptop itself. Arduino Uno micro controller has been interfaced with the laptop using Hardware serial interface. Thus the use of Zigbee or Wi-Fi module has been avoided. These features make our design low cost.
Flow Chart
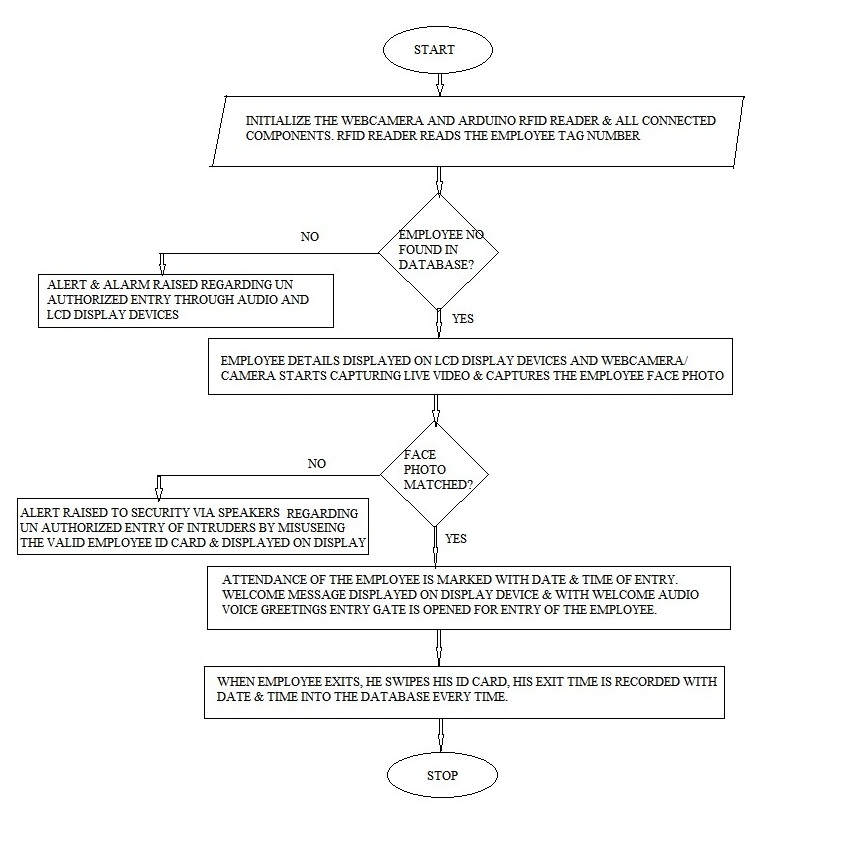
Fig 6: Flow chart of proposed system
WORKING OF THE DESIGN
The screenshot of the hardware implementation of the proposed systems is as shown in fig below.
Whenever the employee enters the campus, he is required to swipe his issued id card from the company. The camera is also placed near the entrance. When the employee swipes ID card number and ID number does not matches with the database then a voice based alert is issued through speaker & security is alerted. The warning alert message is also displayed on display devices.
When the employee swipes ID card number and ID number matches with the database then his face photo is captured from the camera &it’s checked for face detection or face matching with the already existing face photo of the employee from the company database. If the face matches with that present in the database then face matched message is displayed on screen and the employee is asked to enter his left hand thumb impression on finger print sensor.
Once the finger print matches with that present in the database which has been tagged to the particular employee ID number then an audio based voice welcome greetings is played and also welcome message displayed on the display device. We should note that finger print of valid employee trying to give attendance to his colleagues Employee ID will also trigger alarm as the finger print is tested first for valid finger print from the database & if found then its specifically tested for the tagged ID. Thus if employee tries to give proxy then also he gets caught. As discussed above only for valid scenario, Attendance is marked for the employee with the entry time & date details & entry gate is opened for the employee entry. If the scenario is for a valid id card but the face is not matching with that of the present in the database for that particular employee number then an alert is raised via speaker & also warning message is displayed on the display device. Security is immediately alerted through this & hence intruder will captured by the security people. Thus to record the attendance Employee needs to go through three stages of verification such as Valid Employee ID card, face matched then finger print matched. Once these parameters are passed then only the Attendance will be recorded with entry details. Welcome Audio is played and gate is opened & then closed automatically.
When the employee exits then he should swipe his ID card then the exit time is recorded & exit door is opened.Thus even if the intruder successfully gets in using the Valid Employee ID card , with the help of face detection & then Bio-metric authentication he gets caught.
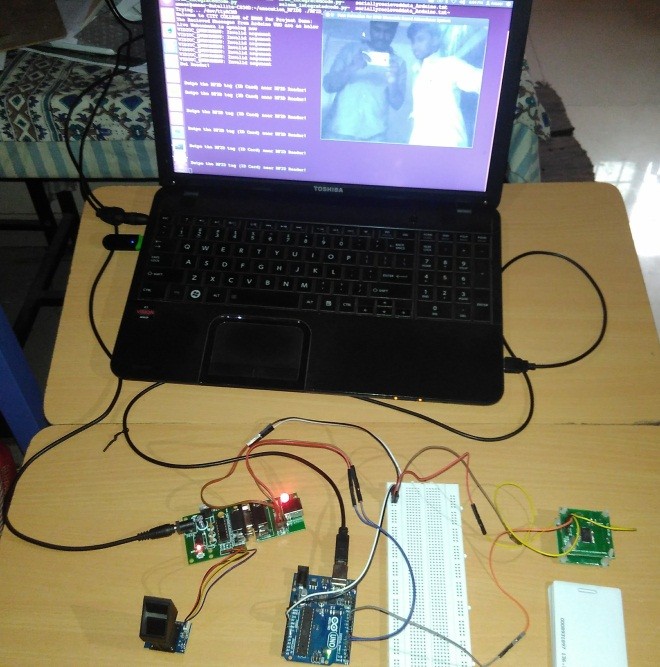
Fig 7: Hardware implementation of proposed system
APPLICATIONS AND ADVANTAGES
- We can write plenty of applications for the proposed system, lets list a few below:
- As Face detection is done, it acts as first layer of security and hence unauthorized use of ID cards is prevented
- Dual or multi people entry with single access card can be prevented
- Finger print authentication used acts as a Third layer security system.
- Attendance recording will be authentic as there is no chance for proxy attendance.
- These kinds of devices can be used in secure and sensitive places where security is of utmost importance. Ex: Secured establishments etc.
- As the proposed design is low cost, hence it can be used in Hospitals, Schools and all government or private firms & establishments .
Disadvantages: One of the disadvantage of the proposed system is the employee needs to undergo multi-layer security checks which will consume some time.
Code for the Implementation of the Project
The code will be shared in the upcoming section with Results.
Note : We will soon update tutorial page. You Can Learn how to create a Project using Arduino and other Micron controllers using those demos.
Author: Venu D
Editor: HelpShareIdeas.com
For giving feedback on this article please mail us at : info@helpshareideas.com
<: Click the link PROJECTS with Code to access the Latest Projects with codes Page:>
Read more




